Tuesday, March 27, 2012
Windows Server 2008 R2: KMS for Windows and Office
KMS for OfficeOffice 2010
-Download the KeyManagementServiceHost.exe
-Open KeyManagementServiceHost.exe
-Type in the KMS key
Client VL for Win 7
Vista Business / Vista Enterprise, Win7 Professional / Win7 Enterprise
KMS A
Windows Web Server 2008 / Windows Server 2008 HPC Edition / Client VL
KMS B
Windows Server 2008 Standard / Windows Server 2008 Enterprise / Client VL
KMS C
Windows Server 2008 Datacenter /Windows Server 2008 für Itanium-based Systems / Client VL
Showing status for Office only:
slmgr.vbs /dlv bfe7a195-4f8f-4f0b-a622-cf13c7d16864
KMS for Windows
Type in the KMS key with the paramaeter:
slmgr.vbs /ipk 12345-12345-12345-12345-12345
Activate the KMS key:
slmgr.vbs /ato
Showing status for Windows KMS Hosts:
slmgr.vbs /dlv
slmgr.vbs /dlv all
You can also check the KMS Events in the Eventviewer:
Monday, March 26, 2012
WDS: Integrate a languagepack with DSIM
Showing the index you have to use!
Dism /get-wiminfo /wimfile:C:\images\Win7.Ent.EN-EN.WIM
Dism /Mount-WIM /WimFile:C:\Images\Win7.Ent.EN-EN.WIM /Index:"1" /MountDir:C:\mount
Now download the language pack you want to integrate and create a directory C:\Scratch, because the files have to save temporally.
Dism /Image:C:\mount /ScratchDir:C:\Scratch /add-package /packagepath:C:\Languagepacks\lpGER.cab
Command to show information about the installed language packs.
Dism /Image:C:\mount /get-Intl
Optional you can add some other Language Packages, if you want.
To save the changes you have to unmount the Image.
Dism /Unmount-WIM /MountDir:C:\mount /Commit
------------------------------------------------------------------------------------------------------------
Set a standard Input System and User-Locale in the XML file
For a standard Input-, System- and User-Locale edit the ImageUnattend.xml:
For German 32bit
<component name="Microsoft-Windows-International-Core" processorArchitecture="x86" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" xmlns:wcm="http://schemas.microsoft.com/WMIConfig/2002/State" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<InputLocale>de-DE; en-US</InputLocale>
<SystemLocale>de-DE</SystemLocale>
<UserLocale>de-DE</UserLocale>
</component>
For English 32bit
<component name="Microsoft-Windows-International-Core" processorArchitecture="x86" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" xmlns:wcm="http://schemas.microsoft.com/WMIConfig/2002/State" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<InputLocale>en-US; de-DE</InputLocale>
<SystemLocale>en-US</SystemLocale>
<UserLocale>en-US</UserLocale>
</component>
WDS: Integrate a hotfix using DSIM
1.Check Index of the wim file
Dism /get-wiminfo /wimfile:c:\images\install.WIM
2.Mount image
Dism /mount-wim /wimfile:c:\images\install.wim /mountdir:c:\mount /index:1
3.Expand the Hotfix with 7zip and extract the cab file

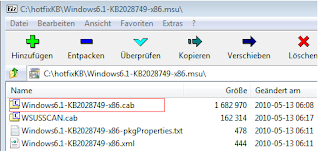
4.Add the cab file to the wim
Dism /image:c:\images\install.wim /add-package /Packagepath:c:\hotfix\Windows6.1-KB2028749-x86.cab
5.Unmount image and commit changes
Dism /unmount-wim /mountdir:c:\mount /Commit
AD: MSI Software Rollout via GPO with groups
In ADUC
Create a global group named "GG-Workstations Department X"
Create a local group in ADUC named "LG-Software XY 9.1.0" and add it to "GG-Workstations Department X"
Add the local group "LG-Software XY 9.1.0" to the Software folder.
In GPO management
Create a gpo for the Software and link it to the right OU
Under tab Scope, Security Filtering and Remove Authenticated Users and add the local group
Right click on the policy and click Edit
Expand Computer Management>Policies>Software Settinsgs>Software installation
Right click Software installation click New> package
Browse to the package
Click Advanced
General Tab: Type in the Software Name, Version, language and location
Deployment: Set "Uninstall this application when it falls ou of the scope of management", Click Advanced and set "Ignore language when deploying this package"
Modifications: For MST files
Security: Remove Authenticated users(Click Advanced,Choose Authenticated Users and deselect Include inheritable… Click Add, After this Aplly and click Yes), add the local group
ADUC: Additional account info in Active Directory Users and Computers
Hi guys,
for getting additional account info in ADUC following the following steps:
Downloading the files:
-acctinfo.dll
-lockoutstatus.exe
Create a shortcut for ADUC runs in 32bit context:
For 32bit using the following cmd
@echo off
echo This program will register the Acctinfo tab Add-on to AD Users and Computers and integrate the lockoutstatus.exe hf TIM
echo.
xcopy lockoutstatus.exe "%systemroot%\system32\" /e /y > nul:
xcopy acctinfo.dll "%systemroot%\system32\" /e /y > nul:
regsvr32 "%systemroot%\system32\acctinfo.dll" /s
exit
For 64bit using this
@echo off
echo This program will register the Acctinfo tab Add-on to AD Users and Computers and integrate the lockoutstatus.exe hf TIM
echo.
xcopy dsa32.lnk "%systemdrive%\Users\%username%\desktop\" > nul:
xcopy lockoutstatus.exe "%systemroot%\syswow64\"/e /y > nul:
xcopy acctinfo.dll "%systemroot%\syswow64\" /e /y > nul:
regsvr32 "%systemroot%\syswow64\acctinfo.dll" /s
exit
for getting additional account info in ADUC following the following steps:
Downloading the files:
-acctinfo.dll
-lockoutstatus.exe
Create a shortcut for ADUC runs in 32bit context:
Save the files to the same location.
For 32bit using the following cmd
@echo off
echo This program will register the Acctinfo tab Add-on to AD Users and Computers and integrate the lockoutstatus.exe hf TIM
echo.
xcopy lockoutstatus.exe "%systemroot%\system32\" /e /y > nul:
xcopy acctinfo.dll "%systemroot%\system32\" /e /y > nul:
regsvr32 "%systemroot%\system32\acctinfo.dll" /s
exit
For 64bit using this
@echo off
echo This program will register the Acctinfo tab Add-on to AD Users and Computers and integrate the lockoutstatus.exe hf TIM
echo.
xcopy dsa32.lnk "%systemdrive%\Users\%username%\desktop\" > nul:
xcopy lockoutstatus.exe "%systemroot%\syswow64\"/e /y > nul:
xcopy acctinfo.dll "%systemroot%\syswow64\" /e /y > nul:
regsvr32 "%systemroot%\syswow64\acctinfo.dll" /s
exit
After you run the cmd restart ADUC and it will give you a new tab:
Thursday, March 22, 2012
AD: GPO Disable Games in Windows XP
Open GPO Management, create a new GPO and go to:
Computer Configuration > Windows Settings > Security Settings > Software Restriction Policies
Rightclick "Additional Rules" and click on "New Path Rule..."
Now type in the following paths:
%SystemRoot%\system32\freecell.exe
%SystemRoot%\system32\mshearts.exe
%SystemRoot%\system32\sol.exe
%SystemRoot%\system32\spider.exe
%SystemRoot%\system32\winmine.exe
C:\Program Files\MSN Gaming Zone
C:\Program Files\Windows NT\Pinball\PINBALL.EXE
AD: Powershell cmdlets
Add-ADDomainControllerPasswordReplicationPolicy
Add-ADGroupMember
Clear-ADAccountExpiration
Disable-ADOptionalFeature
Enable-ADOptionalFeature
Get-ADAccountResultantPasswordReplicationPolicy
Get-ADComputerServiceAccount
Get-ADDomain
Get-ADDomainControllerPasswordReplicationPolicy
Get-ADFineGrainedPasswordPolicy
Get-ADForest
Get-ADGroupMember
Get-ADOptionalFeature
Get-ADPrincipalGroupMembership
Get-ADServiceAccount
Get-ADUserResultantPasswordPolicy
Move-ADDirectoryServer
Move-ADObject
New-ADFineGrainedPasswordPolicy
New-ADObject
New-ADServiceAccount
Remove-ADComputer
Remove-ADDomainControllerPasswordReplicationPolicy
Remove-ADFineGrainedPasswordPolicySubject
Remove-ADGroupMember
Remove-ADOrganizationalUnit
Remove-ADServiceAccount
Rename-ADObject
Restore-ADObject
Set-ADAccountControl
Set-ADAccountPassword
Set-ADDefaultDomainPasswordPolicy
Set-ADDomainMode
Set-ADForest
Set-ADGroup
Set-ADOrganizationalUnit
Set-ADUser
Unlock-ADAccount
AD: Active Directory Tools
Onboard
Event Logs
DCDIAG
Domaincontroller Diagnostic Tools
NETDIAG
Showing issue for the DC network
DNSLINT
For checking DNS
NETSH
DHCP, Network options
Repadmin
Replication tool
Data Collector Sets
Performance Diagnostics for AD, System and more.
FREE Third Party Tools
AD Topology Diagrammer(Visio required)
http://www.microsoft.com/download/en/details.aspx?displaylang=en&id=13380
AD Tidy Free Edition
Query AD for last logged on Attributes of User/Computer accounts. Move Delete and more options available.
http://www.cjwdev.co.uk/Software/ADTidy/Info.html
AD Info Free Edition
Query AD for Information about AD objects
http://www.cjwdev.co.uk/Software/ADReportingTool/Info.html
LIZA
Analyse ACL on Active Directory
http://www.ldapexplorer.com/en/liza.htm
LUMAX
LDAP Explorer and Maintenance
http://www.ldapexplorer.com/en/lumax.htm
Event Logs
DCDIAG
Domaincontroller Diagnostic Tools
NETDIAG
Showing issue for the DC network
DNSLINT
For checking DNS
NETSH
DHCP, Network options
Repadmin
Replication tool
Data Collector Sets
Performance Diagnostics for AD, System and more.
FREE Third Party Tools
AD Topology Diagrammer(Visio required)
http://www.microsoft.com/download/en/details.aspx?displaylang=en&id=13380
AD Tidy Free Edition
Query AD for last logged on Attributes of User/Computer accounts. Move Delete and more options available.
http://www.cjwdev.co.uk/Software/ADTidy/Info.html
AD Info Free Edition
Query AD for Information about AD objects
http://www.cjwdev.co.uk/Software/ADReportingTool/Info.html
LIZA
Analyse ACL on Active Directory
http://www.ldapexplorer.com/en/liza.htm
LUMAX
LDAP Explorer and Maintenance
http://www.ldapexplorer.com/en/lumax.htm
ADUC: Create a custom LDAP Query
To create a custom Saved Query, follow these steps.
- Right-click Saved Queries and click the New-Query option
- Type in a name for your saved query, such as "Search"
- Click the Define Query button
- Under the Find drop-down list, select Custom Search
- Click the Advanced tab
- Type in your query
Finds all disabled User Accounts
Finds all groups that have no members
Finds all locked out User Accounts
Windows Server: Printserver Migration from 2003 to 2008
For a Migration do the following steps:
1. Cleanup the old server.
2. !!!Update all Drivers to x86 and x64 on the old server!!! The x86 and x64 drivers must be the same. Use Universal Print Driver if you can.
Link HP:
http://h20271.www2.hp.com/SMB-AP/cache/380442-0-0-14-121.html
Link Lexmark:
http://www1.lexmark.com/en_US/software/upd/index.shtml
Link Brother:
http://welcome.solutions.brother.com/BSC/public/us/us/en/faq/faq/000000/002700/000074/faq002774_000.html?reg=us&c=us&lang=en&prod=mfc9010cn_us
3. Expand the tree, then right click on Print Servers and click on Add/Remove Servers .
4. Enter the name of the print server you want to migrate the printers off of and select Add to List, then click Apply.
5. Right Click on the server and select Export Printers to a File and save that file.
6. After the export is complete, right click on your new server in the tree.
7. Select Import Printer from a File, and select the export.
8. Follow the wizard…
AD: Well known SIDs in Active Directory
---FOR USERS---
User Well known SID
Creator Owner S-1-3-0
Administrator S-1-5-21domain-500
Guest S-1-5-21domain-501
KRBTGT S-1-5-21domain-502
Interactive S-1-5-4
Anonymous S-1-5-7
---FOR GROUPS---
Group Well known SID
Everyone S-1-1-0
Enterprise Domain Controllers S-1-5-9
Authenticated Users S-1-5-11
Domain Admins S-1-5-21domain-512
Domain Users S-1-5-21domain-513
Domain Computers S-1-5-21domain-515
Domain Controllers S-1-5-21domain-516
Cert Publishers S-1-5-21domain-517
Schema Admins S-1-5-21domain-518
Enterprise Admins S-1-5-21domain-519
Group Policy Creator Owners S-1-5-21domain-520
Administrators S-1-5-32-544
Users S-1-5-32-545
Guests S-1-5-32-546
Account Operators S-1-5-32-548
Server Operators S-1-5-32-549
Print Operators S-1-5-32-550
Backup Operators S-1-5-32-551
Replicators S-1-5-32-552
Pre-Windows 2000 Compatible Access S-1-5-32-554
Remote Desktop Users S-1-5-32-555
Network Configuration Operators S-1-5-32-556
Incoming Forest Trust Builders S-1-5-32-557
Enterprise Read-only Domain Controllers S-1-5-21domain-498
Read-only Domain Controllers S-1-5-21domain-521
Allowed RODC Password Replication Group S-1-5-21domain-571
Denied RODC Password Replication Group S-1-5-21domain-572
Event Log Readers S-1-5-32-573
User Well known SID
Creator Owner S-1-3-0
Administrator S-1-5-21domain-500
Guest S-1-5-21domain-501
KRBTGT S-1-5-21domain-502
Interactive S-1-5-4
Anonymous S-1-5-7
---FOR GROUPS---
Everyone S-1-1-0
Enterprise Domain Controllers S-1-5-9
Authenticated Users S-1-5-11
Domain Admins S-1-5-21domain-512
Domain Users S-1-5-21domain-513
Domain Computers S-1-5-21domain-515
Domain Controllers S-1-5-21domain-516
Cert Publishers S-1-5-21domain-517
Schema Admins S-1-5-21domain-518
Enterprise Admins S-1-5-21domain-519
Group Policy Creator Owners S-1-5-21domain-520
Administrators S-1-5-32-544
Users S-1-5-32-545
Guests S-1-5-32-546
Account Operators S-1-5-32-548
Server Operators S-1-5-32-549
Print Operators S-1-5-32-550
Backup Operators S-1-5-32-551
Replicators S-1-5-32-552
Pre-Windows 2000 Compatible Access S-1-5-32-554
Remote Desktop Users S-1-5-32-555
Network Configuration Operators S-1-5-32-556
Incoming Forest Trust Builders S-1-5-32-557
Enterprise Read-only Domain Controllers S-1-5-21domain-498
Read-only Domain Controllers S-1-5-21domain-521
Allowed RODC Password Replication Group S-1-5-21domain-571
Denied RODC Password Replication Group S-1-5-21domain-572
Event Log Readers S-1-5-32-573
Wednesday, March 21, 2012
AD: Create a Fine-Grained Password Policy
Req.: Windows Server 2008
-Open ADSI Edit
-Go to CN=System, CN=Possword Settings Container
-Right click select New>Object
-Select the class msDS-PasswordSettings and click Next
-Enter the values msDS-Minimum PasswordAge (format Days:Hours:Minutes:Seconds)01:00:00:00
-Assign this policy to a group:
-Open ADSI Edit
-Go to CN=System, CN=Possword Settings Container
-Right click select New>Object
-Select the class msDS-PasswordSettings and click Next
-Enter the values msDS-Minimum PasswordAge (format Days:Hours:Minutes:Seconds)01:00:00:00
-Assign this policy to a group:
Rightclick object
Got to Attribute msDS-PSOAppliesTo
Click Edit and select Add Windows Account. Type in the group name.
Got to Attribute msDS-PSOAppliesTo
Click Edit and select Add Windows Account. Type in the group name.
WDS: Setup WDS with wdsutil
After you adding the WDS role to your Windows Server 2008 R2 you can Setup the WDS using a cmd file.Copy your images and unattend files to the server.
WDSUTILSetup.cmd
cmd = "wdsutil /initialize-server /reminst:F:\RemoteInstall"
cmd = "wdsutil /Set-Server /AnswerClients:all"
cmd = "wdsutil /Add-Image /ImageFile:"C:\boot.wim" /ImageType:Boot"
cmd = "wdsutil /add-image /Imagefile:"C:\capture.wim" /ImageType:Boot"
cmd = "wdsutil /add-Imagegroup /Imagegroup:BasicImages"
cmd = "wdsutil /Add-Image /ImageFile:"C:\Install.wim" /ImageType:Install /ImageGroup:BasicImages"
cmd = "WDSUTIL /Set-Server /WdsUnattend /Policy:Enabled /File:Unattendx86.xml /Architecture:x86"
WDSUTILSetup.cmd
cmd = "wdsutil /initialize-server /reminst:F:\RemoteInstall"
cmd = "wdsutil /Set-Server /AnswerClients:all"
cmd = "wdsutil /Add-Image /ImageFile:"C:\boot.wim" /ImageType:Boot"
cmd = "wdsutil /add-image /Imagefile:"C:\capture.wim" /ImageType:Boot"
cmd = "wdsutil /add-Imagegroup /Imagegroup:BasicImages"
cmd = "wdsutil /Add-Image /ImageFile:"C:\Install.wim" /ImageType:Install /ImageGroup:BasicImages"
cmd = "WDSUTIL /Set-Server /WdsUnattend /Policy:Enabled /File:Unattendx86.xml /Architecture:x86"
WDS: Integrate drivers into a WIM file with DISM
1. Download and install WAIK
2.Mount the Image
Create folders "Images" and "mount" on c:\
BOOT.WIM=>
dism /mount-wim /WimFile:c:\Images\boot.wim /index:2 /MountDir:c:\mount
INSTALL.WIM=>
dism /mount-wim /WimFile:c:\Images\Install.wim /index:1 /MountDir:c:\mount
3. Administrate drivers
-3.1 Get drivers
-dism /image:c:\mount /get-drivers
-3.2 Add drivers
-3.2.1 with *.inf
-dism /image:c:\mount /add-driver /driver:c:\HP7700\heki.inf
-3.2.2 add drivers in a specified folder
-Type in /recurse to install all drivers in one folder
Example:
dism /image:c:\mount /add-driver /driver:c:\drv /recurse
-3.3 Delete driver
-3.3.1 info driver
- dism /image:c:\mount /get-driverinfo /driver:oem1.inf
-3.3.2 delete driver
-Dism /Image:c:\mount /remove-driver /Driver:oem1.inf
4. Image unmount
Dism /unmount-wim /MountDir:c:\mount /commit
5. Adding the Image to the WDS
Delete the old Image and add the new.
If you only replace the old image sometimes the changes will not be applied.
WDS: Skiprearm in Win7 Sysprep Process
Normally you can only capture a Windows 7 Image three times, with the following XML you can skip the rearm process and you can capture unlimited times!
skiprearm.xml:
<?xml version="1.0" encoding="utf-8"?>
<unattend xmlns="urn:schemas-microsoft-com:unattend">
<settings pass="generalize">
<component name="Microsoft-Windows-Security-Licensing-SLC" processorArchitecture="x86" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" xmlns:wcm="http://schemas.microsoft.com/WMIConfig/2002/State" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<SkipRearm>1</SkipRearm>
</component>
</settings>
<cpi:offlineImage cpi:source="wim:c:/Tims/install.wim#Windows 7 ENTERPRISE" xmlns:cpi="urn:schemas-microsoft-com:cpi" />
</unattend>
Save the script to c:\Windows
Invoke sysprep like:
sysprep /generalize /oobe /shutdown /unattend:c:\Windows\skiprearm.xml
skiprearm.xml:
<?xml version="1.0" encoding="utf-8"?>
<unattend xmlns="urn:schemas-microsoft-com:unattend">
<settings pass="generalize">
<component name="Microsoft-Windows-Security-Licensing-SLC" processorArchitecture="x86" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" xmlns:wcm="http://schemas.microsoft.com/WMIConfig/2002/State" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<SkipRearm>1</SkipRearm>
</component>
</settings>
<cpi:offlineImage cpi:source="wim:c:/Tims/install.wim#Windows 7 ENTERPRISE" xmlns:cpi="urn:schemas-microsoft-com:cpi" />
</unattend>
Save the script to c:\Windows
Invoke sysprep like:
sysprep /generalize /oobe /shutdown /unattend:c:\Windows\skiprearm.xml
WDS: Activate Office 2010 after Imaging
This works for an english OS. For other languages change "Program Files".
For Win XP
Create "actOffice10en.bat" under D:\RemoteInstall\Images\ImageGroup\WinXP\$OEM$\$1\adm
actOffice10en.bat
net start "osppsvc"
cd c:\windows\system32\cscript
cscript.exe C:\"Program Files\Microsoft Office\Office14\OSPP.VBS" /act
Aadd the entry in sysprep.inf
[GuiRunOnce]
Command1=c:\adm\actOffice10en.bat
For Win7
Create the SetupComplete.cmd under D:\RemoteInstall\Images\ ImageGroup \Win7\$OEM$\$$\Setup\Scripts
SetupComplete.cmd
net start "sppsvc"
cd c:\windows\system32\cscript
cscript.exe C:\"Program Files\Microsoft Office\Office14\OSPP.VBS" /act
For Win XP
Create "actOffice10en.bat" under D:\RemoteInstall\Images\ImageGroup\WinXP\$OEM$\$1\adm
actOffice10en.bat
net start "osppsvc"
cd c:\windows\system32\cscript
cscript.exe C:\"Program Files\Microsoft Office\Office14\OSPP.VBS" /act
Aadd the entry in sysprep.inf
[GuiRunOnce]
Command1=c:\adm\actOffice10en.bat
For Win7
Create the SetupComplete.cmd under D:\RemoteInstall\Images\ ImageGroup \Win7\$OEM$\$$\Setup\Scripts
SetupComplete.cmd
net start "sppsvc"
cd c:\windows\system32\cscript
cscript.exe C:\"Program Files\Microsoft Office\Office14\OSPP.VBS" /act
Windows: Create a custom MMC for Administration
Subscribe to:
Comments (Atom)





